Airport IoT cyber-security: security validation
- Like
- Digg
- Del
- Tumblr
- VKontakte
- Buffer
- Love This
- Odnoklassniki
- Meneame
- Blogger
- Amazon
- Yahoo Mail
- Gmail
- AOL
- Newsvine
- HackerNews
- Evernote
- MySpace
- Mail.ru
- Viadeo
- Line
- Comments
- Yummly
- SMS
- Viber
- Telegram
- Subscribe
- Skype
- Facebook Messenger
- Kakao
- LiveJournal
- Yammer
- Edgar
- Fintel
- Mix
- Instapaper
- Copy Link
Posted: 15 March 2023 | Arul Gopi | No comments yet
Arul Gopi, Senior Manager – IT Network & Security at Bangalore International Airport, discusses the rise of Internet of Things (IoT) technology and the steps airports must take to secure their airport IT infrastructure.


Bangalore International Airport Limited (BIAL) runs on the introduction of new technologies and innovative solutions that can enhance passenger and stakeholder comfort. In the process, BIAL has the state-of-the-art T2 garden terminal which reflects Bengaluru’s heritage and fame as a garden city. With precise choice of advanced automation, the entire irrigation to the hanging garden in the shape of bells and veils is done.
Airports adopting the Internet of Things (IoT) technology, are not only impacted with their information technology (IT) infrastructure but are also impacted by the operations technology (OT) infrastructure. Another aspect to be considered is that some of these systems operate in or around harsh airport environments.
Unlike IT networks, OT environments have a separation between data-planes using standard protocols such as Modbus, DNP3 and Profinet and control-plane protocols. In fact, it is considered normal for OT environments to consist of extreme temperatures, dirt, fumes, radiation, and so on.
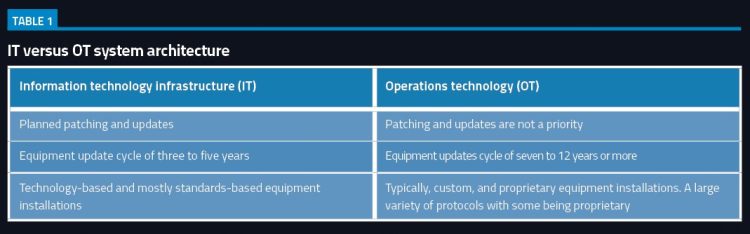

IT versus OT system architecture
Refer to table 1. These two functions, while similar, often have different objectives. The challenge in reducing the growing risks of IoT hacking then lies in securing the ‘information’ generated by the airport’s ‘operational’ assets. Penetration testers face challenges when testing on the control plane side of a network.
Here are examples of a Security Validation Checklist for evaluating and resolving the cyber risks in their OT:
1. PCB-Chips-Circuit
- Any removed IC / model names?
- Any connected pins?
- Any uncleared trace paths?
- Is tamper response (like critical memory erase, noise generators, epoxy layer on PCBs, security fuses) adopted in design?
- e. Have emission prevention by providing shielding mechanisms?
2. Firmware:
- Is firmware encrypted?
- Secure boot trusted platform modules for crypto engines
- Any dummy code in flash above the memory partitioning
- Check for programming practices established for managing buffer overflows
- Check for the quality assurance procedures
- Ensure any software reverse engineering cannot happen through faults in code
3. Operating system:
- Ensure latest stable OS
- Ensured that users/applications cannot write to the root file system Implementing an encrypted file system
- Removed all libraries that are redundant
- Disabled all ports, protocols and services that are unused
- Ensure that the software’s installed is from trusted sources.
4. Data storage:
- Check for credential management in place
- Ensured SAM, TPM for store credentials or encryption keys MCU in place to control access of memory protection unit in embedded OS.
5. Remote monitoring:
- Check for authorisation and authentication techniques in place
- Ensured integrity of sessions and cookies that are to be maintained
- Check for encryption of logins and password credentials in place.
The world of the Internet of Things is, without a doubt, the future of technology. However, with the rise in popularity of IoT products, we also see an increase in the number of vulnerabilities found in those products.
IoT security threats are a reality. U.S. Department of Homeland Security information shows a seven-fold increase in IoT incidents. DC Researchers estimate that 10 per cent of attacks will target IoT and airports must secure their OT connected systems and networks.
Airports must mitigate risks while capitalising on IoT by laying strong foundations for future risk-management with secured IoT, preparing for the work through programs and procedures to deal with disruptions and ensure meaningful collaboration between the IT and OT experts.


Issue
Related topics
Cyber-security, Data, Digital transformation, Information technology (IT), New technologies, Security


















