Mitigating and preventing the effects of a security breach with a simple bowtie
- Like
- Digg
- Del
- Tumblr
- VKontakte
- Buffer
- Love This
- Odnoklassniki
- Meneame
- Blogger
- Amazon
- Yahoo Mail
- Gmail
- AOL
- Newsvine
- HackerNews
- Evernote
- MySpace
- Mail.ru
- Viadeo
- Line
- Comments
- Yummly
- SMS
- Viber
- Telegram
- Subscribe
- Skype
- Facebook Messenger
- Kakao
- LiveJournal
- Yammer
- Edgar
- Fintel
- Mix
- Instapaper
- Copy Link
Posted: 8 January 2019 | Emma Verschoor | No comments yet
Following the Airport IT & Security conference at the end of 2018, Emma Verschoor from CGE Risk Management Solutions, discusses how CGE’s bowtie diagram highlights threats in an airport to mitigate and prevent the effects security breaches can have.


In December 2018, we attended International Airport Review‘s IT and Security event at Amsterdam Airport Schiphol. This event was all about aviation security and technology and how one can inform the other. We were there to represent CGE’s software products, which centre around risk management solutions through our BowTieXP virtual risk assessment model, which highlights possible issues.
At CGE we do not call ourselves industry experts, but are the bowtie experts. That is one of the reasons we work with more than 200 partners globally. However, we are still aiming to see the application of bowties in the different industries. Barrier management is not very well known in the airport security industry, and as such we have created an overview of bowtie to highlight what can go wrong.
An overview of bowtie
We created a bowtie to understand what airport security is and the possible threats faced by airport security personnel. The bowtie below is not a typical bowtie as we have previously discussed for International Airport Review, but as long as it helps us understand risks, it must be looked upon favourably. The aim of this bowtie is to have an overview of unwanted events and their potential causes. If we are aware of what the potential risks are, we are more prepared to deal with the consequences of the threat.
The hazard for this bowtie (the top box of the middle section of the diagram) is ‘security operations at airport’. Although quite generic, it fits the purpose of this bowtie. The top event, or the loss of control moment, is a security breach (the centre of the diagram). “A security breach is any incident that results in unauthorised access of data, applications, services, networks and/or devices by bypassing their underlying security mechanisms. […] A security breach is also known as a security violation1″.
Now that we have set the scope of this bowtie, we would like to focus first on the consequences on the right side. At the conference, the issue of human trafficking was discussed, alongside with the responsibilities airports have to identify possible at-risk targets. At first, we thought airport security is all about preventing bombs blowing up, but it is much more than that. For example, human trafficking is an issue where airports play important roles. At the conference, someone shared their personal experiences with human trafficking and how airports can help identify signs of human trafficking. Also, international migration can be a security issue, and although it does not directly cause harm, it is an issue that needs to be managed.
There are probably many more issues to deal with in airport security, more specifically threats. The threats are the potential causes that can lead to any security breach. Be aware that not all threats can lead directly to all the consequences, but we did want to highlight issues on mental health. Multiple speakers mentioned mental issues as a large threat to security. In this bowtie, we separated the different issues on mental health, because they need different approaches.
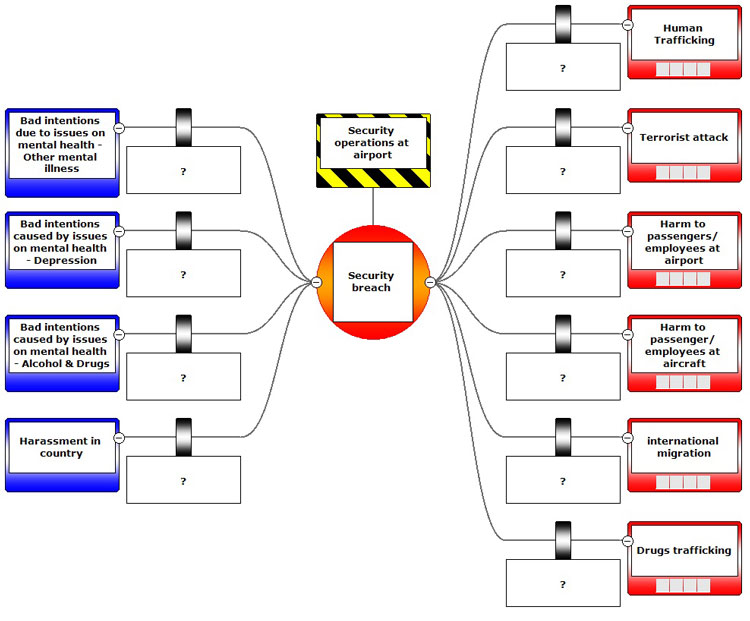

As you can see in the bowtie, there are no barriers. The industry knows exactly what can go wrong, but they do not speak the barrier language yet. Many speakers at the event emphasised that training is key in securing these events, but can we specify what those barriers are? We are sure most organisations can do that and we believe bowties help in this process of defining barriers.
To conclude, there is still a lot to learn about airport security and we think there are many more bowties to specify the security issues.
Are you curious to learn more about bowties in security?
Reference
- Techopedia Inc. (2018, December 12). Security Breach. Retrieved from Techopedia: https://www.techopedia.com/definition/29060/security-breach
Biography
Emma Verschoor is part of the product management team of CGE Risk Management Solutions. She has a degree in Aviation Logistics from the University of Applied Sciences, Amsterdam. This university closely works with industry professionals, such as Amsterdam Airport Schiphol and KLM Royal Dutch Airlines. The aviation department focuses on the logistical streams within the aviation system. After her graduation, CGE Risk Management Solutions invited Emma to be part of the safety specialists and product management team, where she provides training and implementation support in using barrier-based risk management.
Related topics
Airport crisis management, Regulation and Legislation, Risk Management Solutions, Safety, Security, Terminal operations

















